寂井浮廊
打赏我
欢迎您:
游客
登录
发现BUG请联系jintianhu2000@126.com
常用
加解密算法
常用工具
EMV相关
还珠楼论坛
答题闯关
用户信息
帖子列表
语法介绍
帖子详情
ANSI X9 TR31示例摘抄
jin.th 发布于2019-07-23 16:28
[评论区]
[我要回复]
[下载md文件]
[下载pdf文件]
仅自己可见
***群友磊磊提供*** ## A7.2 : Key Block Without Optional Blocks #### A7.2.1 Using Key Variant Binding Method** KBPK: 89E88CF7931444F3 34BD7547FC3F380C PEK: F039121BEC83D26B 169BDCD5B22AAF8F KBEK 使用的常量参数:0x45('E') KBMK 使用的常量参数:0x4D('M') 1)计算KBEK和KBMK KBPK XOR 0x45...0x45: 89E88CF7931444F3 34BD7547FC3F380C XOR 4545454545454545 4545454545454545 = CCADC9B2D65101B6 71F83002B97A7D49 KBPK XOR 0x4D...0x4D: 89E88CF7931444F3 34BD7547FC3F380C XOR 4D4D4D4D4D4D4D4D 4D4D4D4D4D4D4D4D = C4A5C1BADE5909BE 79F0380AB1727541 2)构造KBH KBH属性: 1.仅加密 KBH[8]='E' (0X45) 2.本密钥不使能版本 KBH[9:10]='00' (0X3030) 3.本密钥仅在可信密钥下导出 KBH[11]='E' (0X45) 4.无可选块 KBH[12:13]='00' (0X3030) 字符串表示的KBH:__A,0072,P0,T,E,00,E,00,00__ 16进制ASCII表示:__4130303732503054 4530304530303030__ 3)构造密钥数据: 密钥长度+PIN密钥+pad: 密钥长为16字节,即128bit位,表示为16进制80 pad随机数设为:720DF563BB07 0080 F039121BEC83D26B169BDCD5B22AAF8F 720DF563BB07 4)TDEA-CBC-MAC加密密钥数据 明文:0080 F039121BEC83D26B169BDCD5B22AAF8F 720DF563BB07 IV = KBH的前8字节4130303732503054 密钥为KBEK =》CBC密文:__F5161ED902807AF26F1D62263644BD24192FDB3193C73030__ 5)计算MAC__(见ISO 16609-2004)__ 对KBH明文+KEY数据密文计算MAC MAC计算输入数据: 4130303732503054 4530304530303030 F5161ED902807AF26F1D62263644BD24192FDB3193C73030 KBMK: C4A5C1BADE5909BE 79F0380AB1727541 3DES,Pading Method 1(不填充)方式计算MAC结果= >__1C EE 87 01__73 D7 AD AF 6)构造完整的Key Block 字符串形式:(72个字符) **A0072P0TE00E0000 (16个字符)+** **F5161ED902807AF26F1D62263644BD24192FDB3193C73030 (48个字符)+** **1CEE801 (8个字符)** 把字符串转为ASCII码的16进制(72个字节): **4130303732503054 4530304530303030 463531363145443930323830374146323646314436323236333634344244323431393246444233313933433733303330** **31434545383031** #### A7.2.2 Using Key Derivation Binding Method KBPK: DD7515F2BFC17F85 CE48F3CA25CB21F6 PEK: 3F419E1CB7079442 AA37474C2EFBF8B8 1)构造KBH KBH属性: 1.仅加密 KBH[8]='E' (0X45) 2.本密钥不使能版本 KBH[9:10]='00' (0X3030) 3.本密钥仅在可信密钥下导出 KBH[11]='E' (0X45) 4.无可选块 KBH[12:13]='00' (0X3030) 字符串表示的KBH:__B,0080,P0,T,E,00,E,00,00__ 16进制ASCII表示:4230303830503054 4530304530303030 2)构造key data 密钥长度+PIN密钥+pad: 密钥长为16字节,即128bit位,表示为16进制80 pad随机数设为:1C2965473CE2 **0080 3F419E1CB7079442AA37474C2EFBF8B8 1C2965473CE2 (24字节)** 3)衍生KBEK和KBMK 第一步:计算子密钥K1和K2 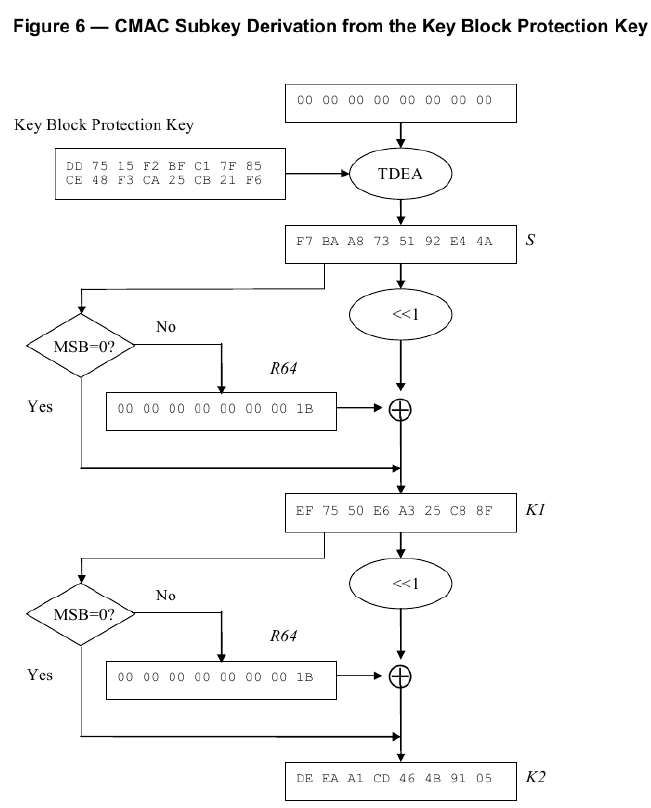 K1 = EF7550E6A325C88F K2 = DEFAA1CD464B9105 第二步:使用K1和KBPK计算KBEK和KBMK 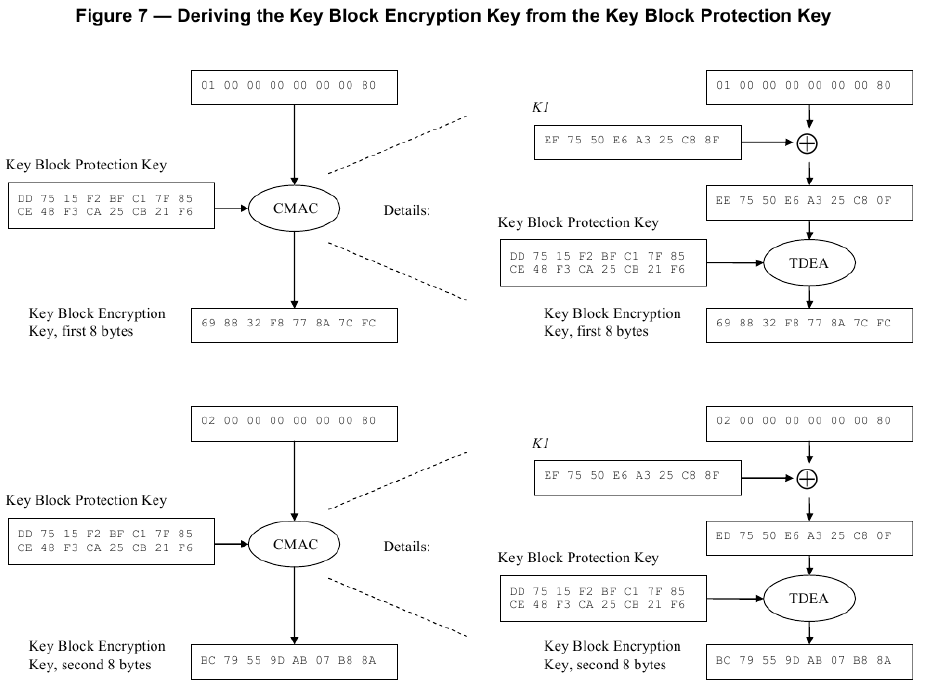 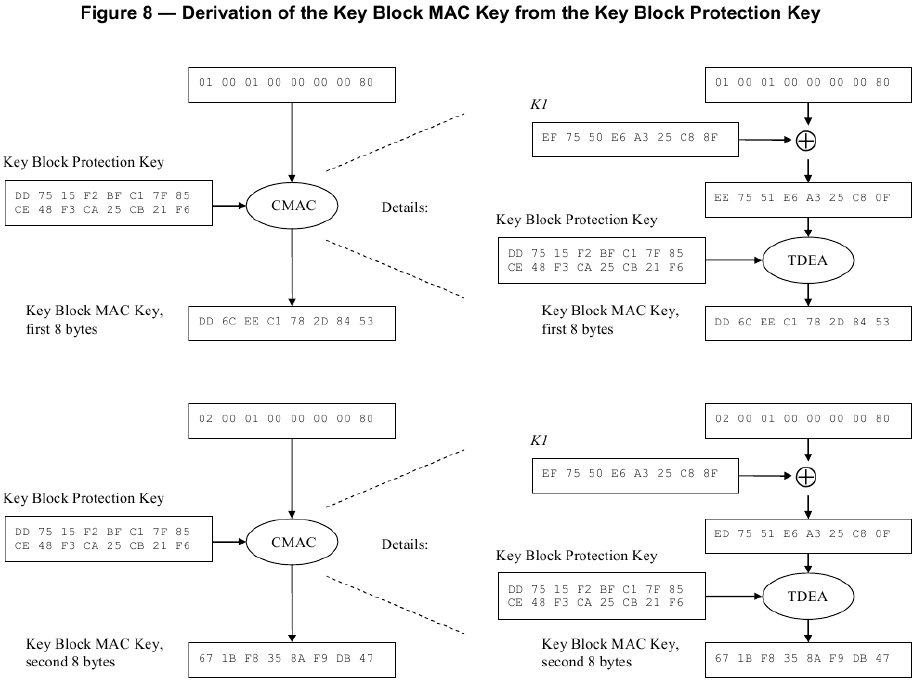 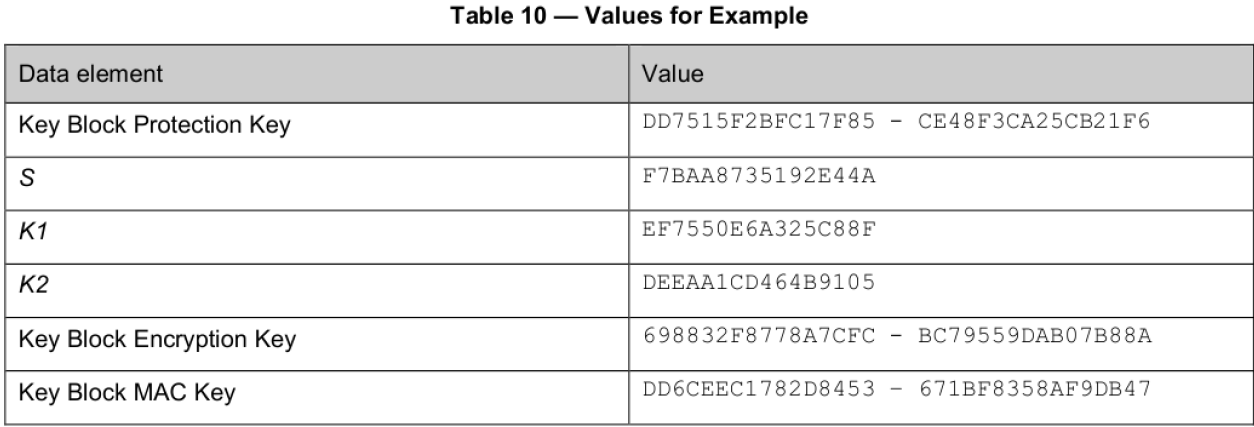 KBEK = 698832F8778A7CFC BC79559DAB07B88A KBMK = DD6CEEC1782D8453 671BF8358AF9DB47 4)计算MAC__(见NIST SP 800-38B)__ 第一步:从KBMK 衍生子密钥KM1和KM2 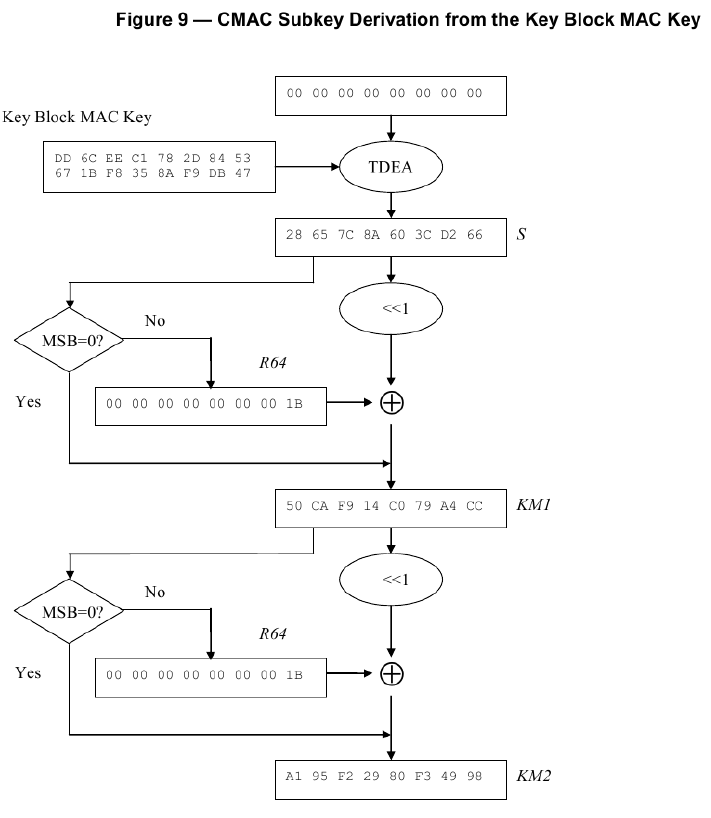 KM1 = 50CAF914C079A4CC MAC输入数据 HBK + Key Data: **4230303830503054 4530304530303030** **00803F419E1CB707** **9442AA37474C2EFB** **F8B8 1C2965473CE2** **最后一个block的处理与2K-3DES-MAC不同。(见NIST SP 800-38B)** 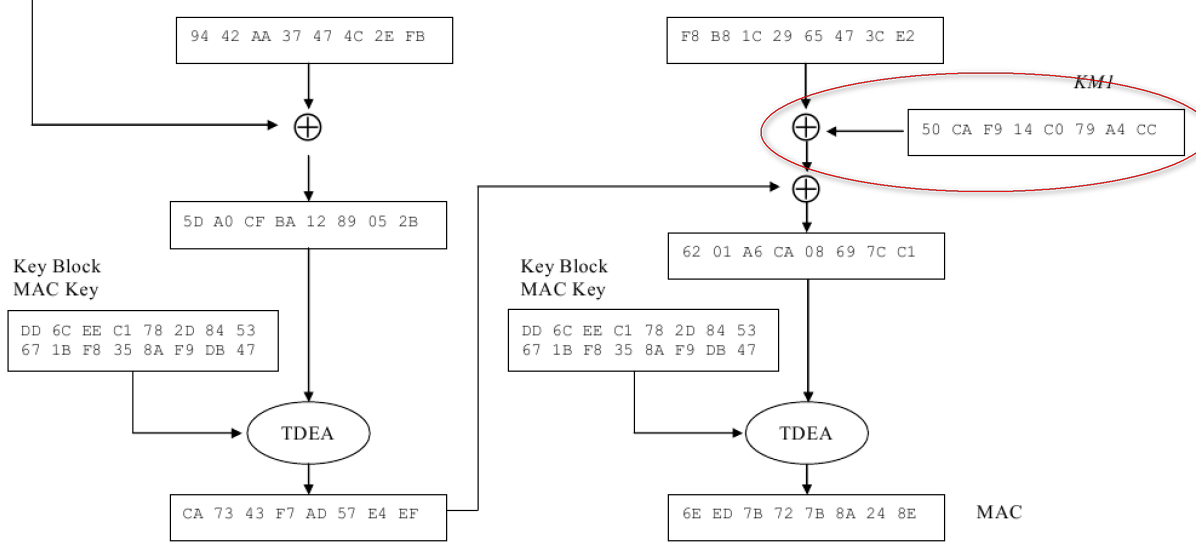 **输出MAC值:** **6EED7B727B8A248E** 5)计算密文 IV: (MAC) 6EED7B727B8A248E **输入数据:0080 3F419E1CB7079442AA37474C2EFBF8B8 1C2965473CE2 (24字节)** **密钥(KBEK)**698832F8778A7CFC BC79559DAB07B88A **加密算法2K-3DES-CBC:** **加密结果:** **94B420079CC80BA3461F86FE26EFC4A3B8E4FA4C5F534117** 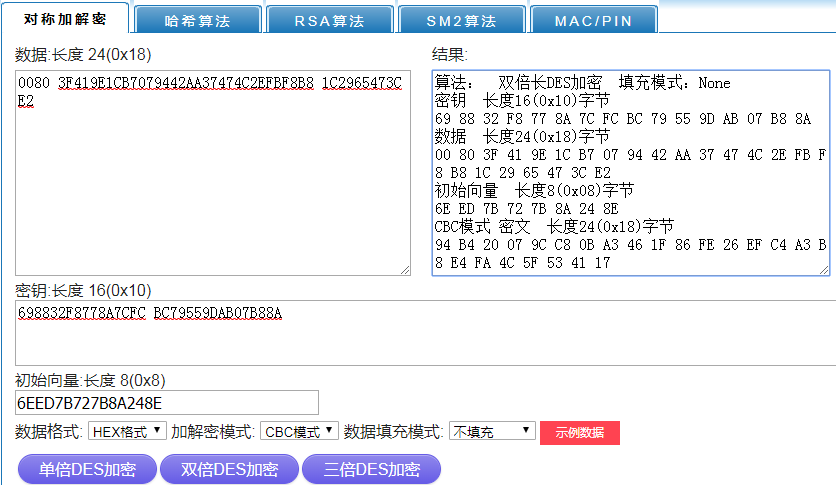 6)把4)和5)的计算结果转为ASCII的16进制形式 **94B420079CC80BA3461F86FE26EFC4A3B8E4FA4C5F534117 = >** 3934423432303037 3943433830424133 3436314638364645 3236454643344133 4238453446413443 3546353334313137 **6EED7B727B8A248E= > 36454544374237323742384132343845** 7)构造完整的Key Block 字符串形式:(80个字符) **B0080P0TE00E0000 (16个字符) +** **94B420079CC80BA3461F86FE26EFC4A3B8E4FA4C5F534117(48个字符)+** **6EED7B727B8A248E(16个字符)** **= >** 4230303830503054453030453030303039344234323030373943433830424133343631463836464532364546433441334238453446413443354635333431313736454544374237323742384132343845
评论列表
回帖
浙ICP备17051204号